From December 13 to 15, my school participated in the HackTheBox University 2024 CTF. This write-up covers the solution to one of the hard web challenges we encountered.
Intergalactic Bounty - Hard
The Galactic Bounty Exchange—a system where hunters and hunted collide, controlled by the ruthless Frontier Board. Hidden within its encrypted core lies a prize of untold power: the bounty for the Starry Spur. To ignite rebellion, Jack Colt must infiltrate this fortress of contracts, manipulate its algorithms, and claim the Spur’s bounty for himself. A race against time, a battle against the galaxy’s deadliest system—Jack’s mission will decide the fate of the Frontier.`
📜 Recognition
The source code for the application was provided. After a brief analysis, a few points stood out:
- The app included a bot file, hinting at a client-side vulnerability.
- There was an email application feature.
- The backend was implemented with JavaScript files.
Now let’s see how the application work :
Upon accessing the application, we were greeted with a registration panel. When attempting to register, it became apparent that only certain email domains were allowed.

Given the presence of a bot file, I hypothesized the following attack chain:
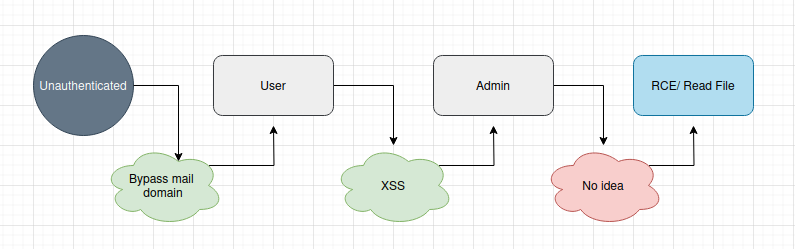
🕵️ Exploitation
Here’s the code for the registration endpoint:
|
|
This revealed two key points:
- The email domain restriction needed bypassing.
- A mass assignment vulnerability allowed us to set the role field in the payload, potentially escalating privileges.
|
|
Once registered, the generated token confirmed our elevated privileges:
|
|
That sounds great! We’re already admins, which seems unintended since we no longer need to find an XSS vulnerability to steal the bot token. Upon further investigation, I discovered what might be an SSRF vulnerability through a functionality that becomes accessible once registered as an admin on the application.
When testing locally, we noticed that bypassing the domain restriction allows us to receive the OTP code required for login, as shown in the screenshot below:
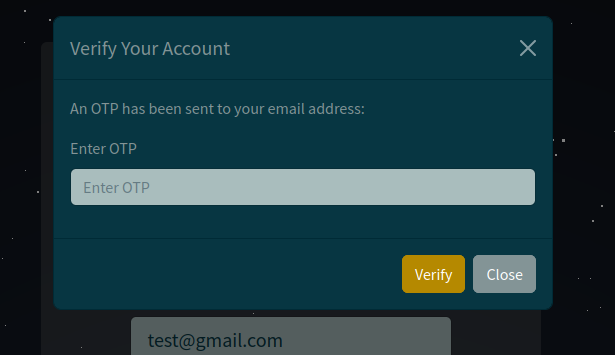
OTP code required to verify our account
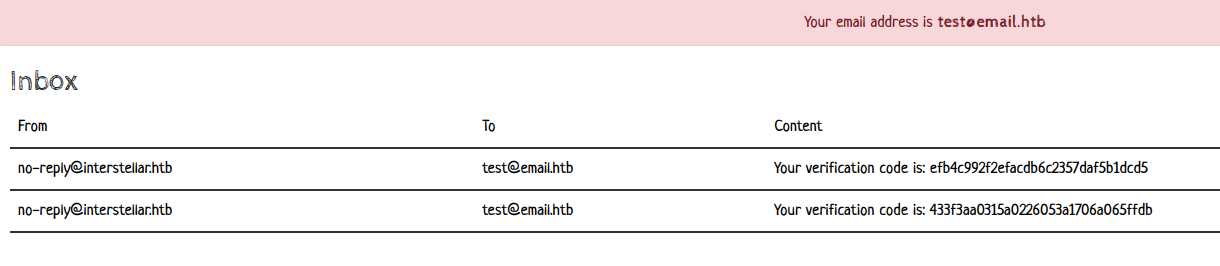 OTP code required to verify our account
OTP code required to verify our account
Now that we know we need to send an email to test@email.htb, we attempted to bypass the parsing logic of the email-addresses library. However, after multiple tests, one of my teammates discovered an alternative method to bypass it. When the application sends us an email via the MailHog app, the following request is executed:
|
|
You see where this is going, right ? What happens if we provide a list of emails instead of a single string ?
|
|
Exactly! When we provide a list of emails, the email lands in the Mailhog app, effectively bypassing the domain restriction. 🎉
To summarize:
- We became admin due to a mass assignment vulnerability.
- We discovered an SSRF vulnerability through the
/transmitendpoint, which is only accessible once registered as an admin.
Here’s the code for reference:
|
|
Why did the challenge maker choose to use Needle? Keep that in mind.
Fun fact : We believe the real way to become admin was this:
- 0-day on the parser of the email-addresses library
- exploiting mutation XSS in the app because the sanitizeHTML function wasn’t very secure.
|
|
After a couple of hours testing ways to read files or achieve RCE on the application, we focused on the Needle documentation and found this option :
|
|
The hypothesis was as follows: “If we can perform a prototype pollution attack and add the option output: ‘/app/index.js’, Needle will overwrite the /app/index.js file and execute our malicious code since the server is set to auto-reload.”
Before attempting prototype pollution, we tested overwriting the file on the app by manually setting the output option in Needle and it worked! Now, let’s find a way to achieve prototype pollution!
After spending more than a day analyzing the code, we quickly noticed that the use of the mergedeep library was particularly interesting, as mergedeep functions are often vulnerable to prototype pollution. Here’s the part of the code where mergedeep is used :
|
|
It’s interesting because this API endpoint can only be called once we are registered as an admin, so it seems we are on the right track. 😉
By fetching this API endpoint as follows, we can trigger prototype pollution:
s.put(WEB_URL + "api/bounties/1", json={"__proto__":{"output":"/app/index.js"}}, headers={"Cookie":"auth="+token}).text)
And then, we can overwrite the file by using the Needle feature. (Note that the compressed option is set to True in Needle, so you need to zip the file before sending the request with Needle).
🤭 Final script
Here the final script written by Woody :
|
|
And here the flag : HTB{f1nd1ng_0d4y_15_345Y_r1gh7!!?_97c10223cada67794bcc9584b943c9e5}
This challenge was a lot of fun! I think it was a bit easier than expected by the challenge maker, thanks to some unintended bypasses like the mass assignment to become admin. Big thanks to my teammates—I’ve learned so much from them, and I definitely wouldn’t have been able to flag this challenge alone; it was really a team effort! 😊
Also, I’m super happy to be part of the school team and to reach second place again this year! 🎉
![Featured image of post [CTF HTB University 2024] - Intergalatic Bounty](/p/ctf-htb-university-2024-intergalatic-bounty/cover.jpg)