Butters Adventure v2
Scenario
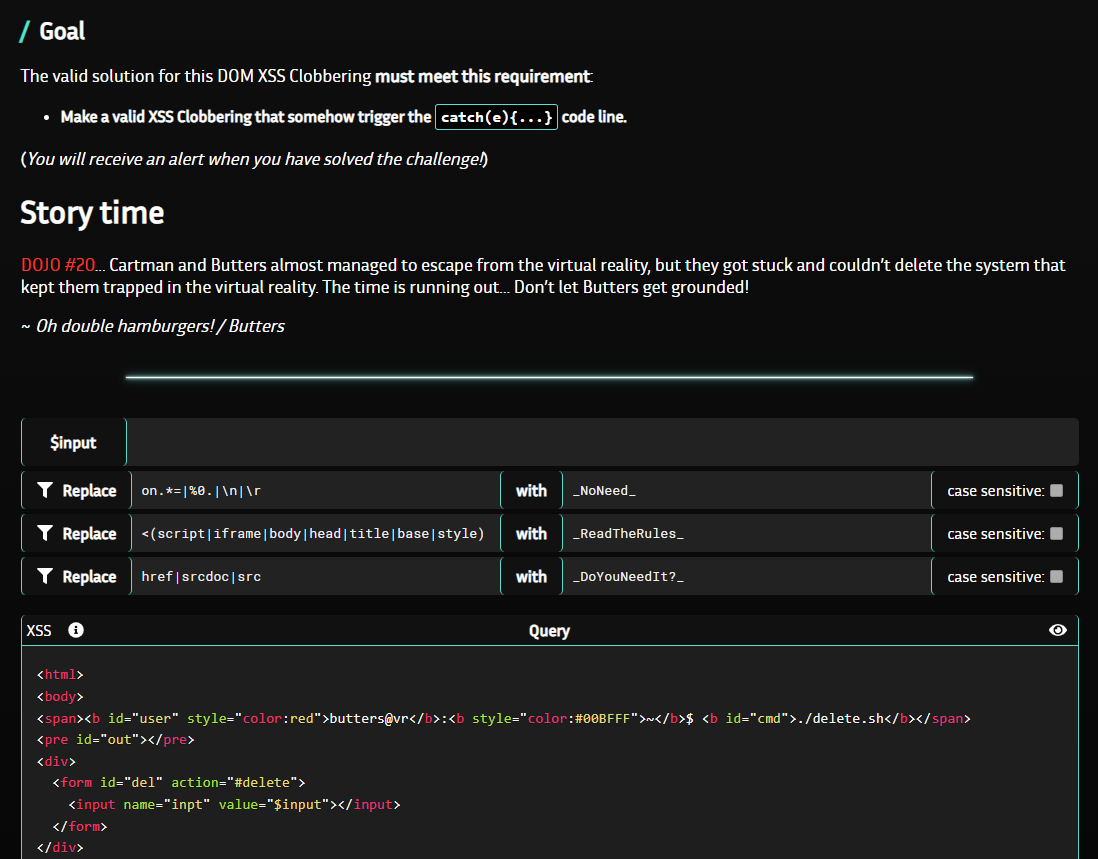
Definition : DOM Clobbering is an attack where injected HTML may confuse the existing JavaScript application and therefore change the application logic.
Code overview Below is the html code used in this challenge :
|
|
First of all, we know that we must catch(e){…}, and that we can perform an html injection in the < input > tag named “inpt” contained in the < form >.
We also have some restrictions regarding the html tags we must use to solve this dojo :
Exploitation We know that to achieve our goal we need to create a new tag with the same name as a function called in the script, so when the function is called it will return the html element we created.
So what happens in the application if we create an html tag with a name like getElementById?
PoC For that we can try this payload :
|
|
Here we gonna to escape the < input > tag, and create an < img > tag with name=getElementById as we can see in the image below.

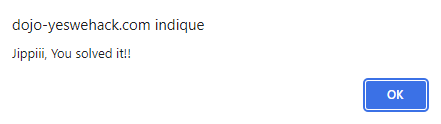
If we inject this payload we can see that we have caught an exception and we have the alert.
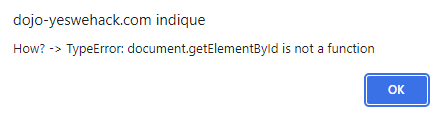
As expected, the error is TypeError: document.getElementById is not a function, because when the function is called, the DOM will return the tag we injected.
Remediation Before working with objects or functions, make sure to verify their legitimacy. When filtering the DOM, it’s important to ensure that the object or function you’re dealing with is not a DOM node. To write better code, be mindful of common mistakes. For example, it’s best to steer clear of using global variables together with the logical OR operator. To protect against security vulnerabilities related to DOM-clobbering, it’s recommended to use a reliable library like DOMPurify that has been thoroughly tested.
![Featured image of post [YesWeHack] - Dojo 22](/p/yeswehack-dojo-22/DOJO-22.jpg)