Description
Reflected XSS attacks, also known as non-persistent attacks, occur when a malicious script is reflected off of a web application to the victim’s browser.
POC
You simply have to set the payload in the ${txt} field. Payload : < img src=x onerror=alert()>
To change the value in the ${txt}, you need to change the css of the page like that :
|
|
The !important rules is very important to keep the CSS configuration.
Xss alert :
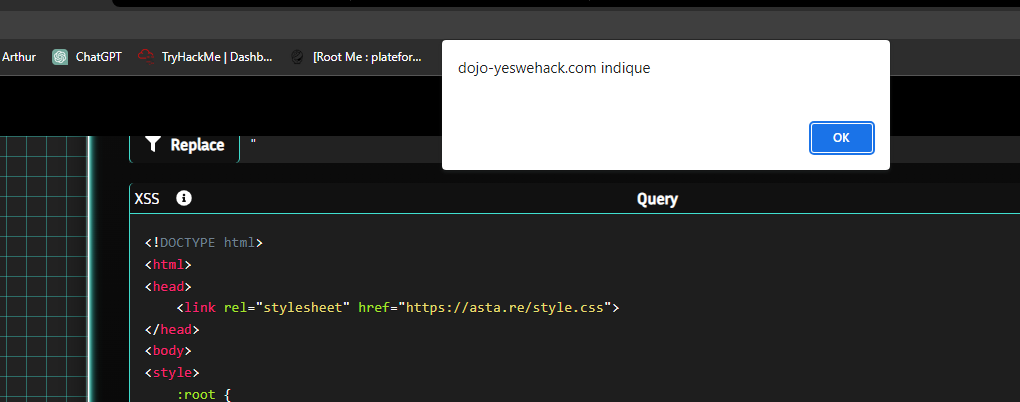
Risk
Cross site scripting attacks can have devastating consequences. Code injected into a vulnerable application can exfiltrate data or install malware on the user’s machine. Attackers can masquerade as authorized users via session cookies, allowing them to perform any action allowed by the user account.
XSS can also impact a business’s reputation. An attacker can deface a corporate website by altering its content, thereby damaging the company’s image or spreading misinformation. A hacker can also change the instructions given to users who visit the target website, misdirecting their behavior. This scenario is particularly dangerous if the target is a government website or provides vital resources in times of crisis.
Remediation
You need to sanitize the data. You can use HTTPOnly cookie flag. You can also implement a Content Security Policy.
![Featured image of post [YesWeHack] - Dojo 25](/p/yeswehack-dojo-25/DOJO-25.jpg)