Description
Server-Side Template Injection (SSTI) is a web security flaw where attackers inject malicious code into server-side templates. This allows them to execute arbitrary commands on the server, potentially leading to data breaches or unauthorized access.
Exploitation
First of all, we documented ourselves on the Velocity template. Reading the documentation we notice that it is possible to declare variables or functions in different ways. To bypass the regex, we therefore notice that it is possible to use $!variable instead of $variable, and for functions it is possible to do #{functions} instead of #function.
Now we are going to look at RCE, by searching on the internet we can find this payload:
|
|
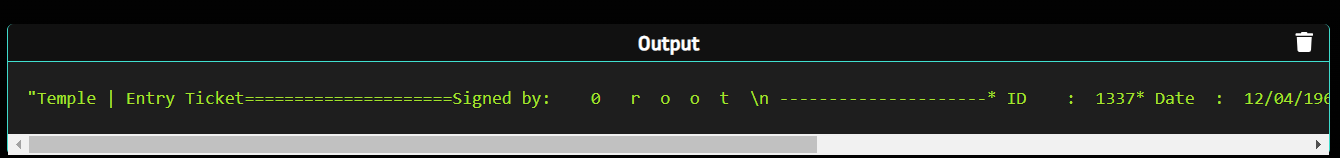
by applying our bypass to the payload we obtain the following poc
PoC
Risk
The risk of executing system code lies in the potential for unauthorized access and control over a system. When an attacker successfully executes system code, they can manipulate or compromise the server, access sensitive information, and potentially launch further attacks on the system.
Remediation
Developers can prevent SSTI by validating and sanitizing user input and adopting secure coding practices.
![Featured image of post [YesWeHack] - Dojo 28](/p/yeswehack-dojo-28/DOJO-28.jpg)